A Complete Guide to Access Tokens, Refresh Tokens, and Their Role in Enhancing Application Security
Access Tokens
Access tokens are the token that confirms whether the specific user is authorized to perform a particular action in an application or not.
Tokens are useful as they reduce the multiple login for authorization inconvenience of the user .
These tokens have less expiry time.
Refresh Tokens
Refresh tokens are generated similarly as access tokens
Refresh tokens are stored in databases.
they are used to generate new access tokens whenever there is a need for authorisation and the access token has expired.
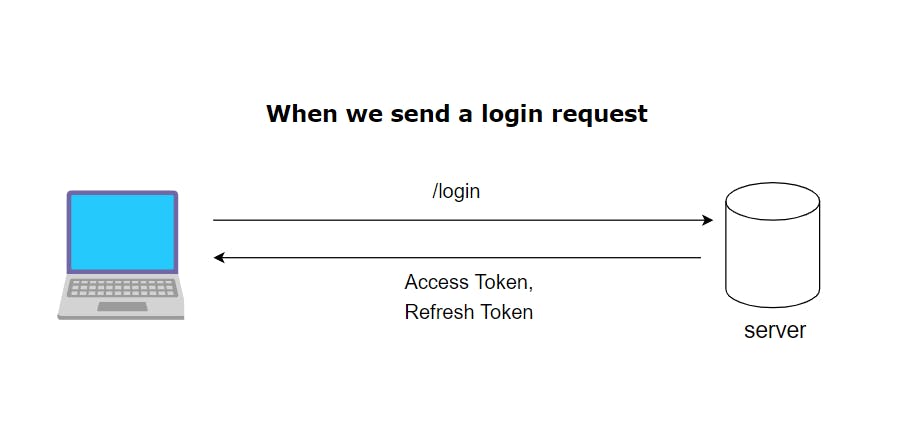

We can use Access Token with extended expiry but still we use Refresh tokens why?
Refresh tokens are used as a security measure to mitigate the risks associated with continually extending the expiration time of access tokens. it's possible to increase the expiry time of access tokens, doing so increases the window of opportunity for an unauthorized party to misuse a stolen or leaked token. Refresh tokens, on the other hand, allow for a more secure and controlled process of obtaining new access tokens without having to store user credentials or reauthenticate the user.
When an access token is close to expiration or has expired, the refresh token can be used to obtain a new access token. This eliminates the need to constantly extend the expiry time of access tokens and reduces the potential impact of a compromised access token. It also provides an additional layer of security by requiring the client to present the refresh token during the token refresh process.
Overall, the use of refresh tokens enhances security by minimizing the exposure of access tokens and providing a more robust approach to obtaining new access tokens when needed.
Model methods that generate the token .
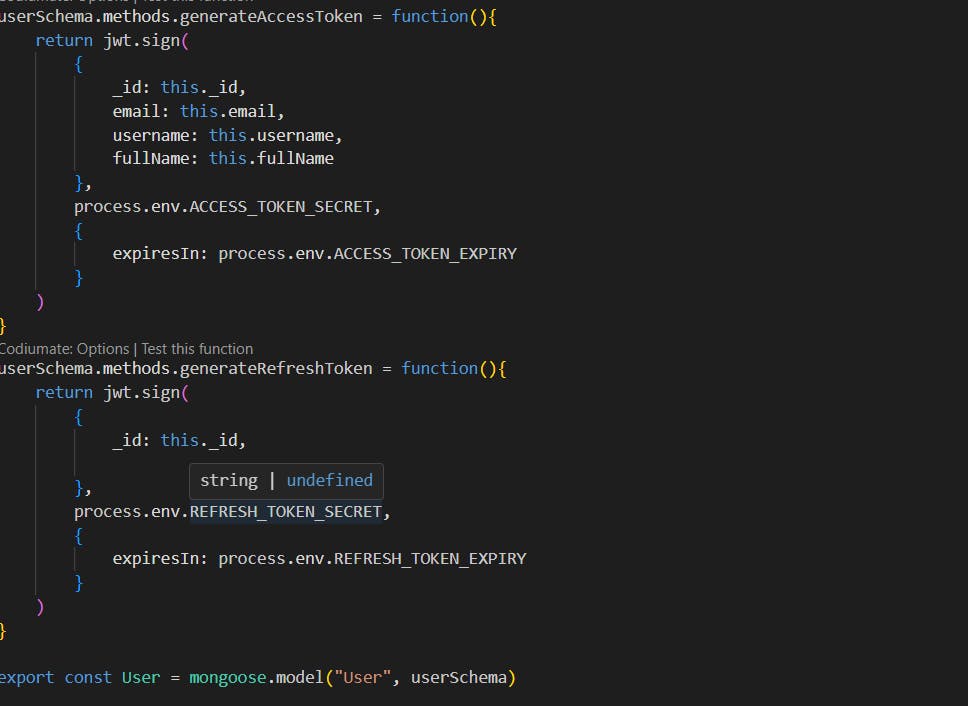
Controllers that generate and save the new refresh token in the Database when refresh is triggered